CRTP Review
Overview:

This was my first time working with altered security, and the course was focused on Active Directory, emphasizing native Red Team tactics rather than Command and Control, like the CRTO. However, the option to leverage Sliver C2 was present, but not required.
Course:
Attacking and Defending Active Directory (Certified Red Team Professional) Lab is designed to provide a platform for security professionals to understand, analyze and practice threats and attacks in a modern Active Directory environment. The lab is beginner friendly and comes with a complete video course and lab manual. The course and the lab are based on our years of experience of making and breaking Windows and AD environments and teaching security professionals.
Exam:
The Certified Red Team Professional is a completely hands-on certification. To be certified, a student must solve practical and realistic challenges in our fully patched Windows infrastructure labs containing multiple Windows domains and forests. The certification challenges a student to compromise Active Directory by abusing features and functionalities without relying on patchable exploits. Students will have 24 hours for the hands-on certification exam.
Why did I even take this Course/Exam:
Now, as you, the reader, may know, I already have the CRTO certification, which some might argue is essentially the same thing. I had a similar thought before purchasing the course as well; however, I wanted to refresh my Active Directory exploitation skills and gain knowledge about Defender and ASMI.
I personally felt that the course was definitely worth it. However, some may say I wasted money, but regardless, that is for each individual to decide after reviewing both options.
The course material:
I purchased the On-Demand Lab 30-day access package on December 13th, 2024, for $249. I opted for the shortest duration, as I already had a firm grasp on these concepts and wanted to complete the material at my own pace. Once purchased, you gain permanent access to the course material, which is available for download from a cloud drive and consists of lecture videos, lecture slides, lab tools, and the lab guide.
I started my lab access on December 14th, as I wanted to attempt the exam before 2025. My methodology was to review each section, update and modify my "Attack Matrix", and follow along with the course lectures, adding notes based on the topic discussions.
The lectures were so enjoyable! Nikhil Mittal made the video feel genuine and unscripted. Many times, things wouldn't work as expected, and he would go with it, explaining alternate methodologies or troubleshooting techniques, which was truly awesome. In addition to the content, he shared practical stories and made occasional funny comments that had me laughing out loud a few times. I believe the lectures alone are worth the price.
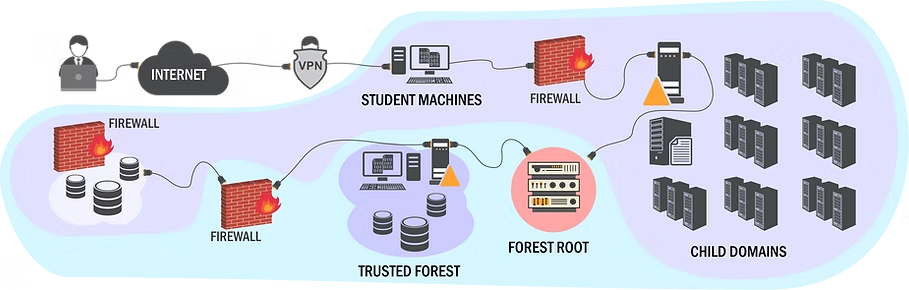
In regard to the lab, it was very stable, and I had only one issue, which was addressed by the Discord staff within two hours (the issue occurred after normal hours, so I didn’t expect a reply until the next day anyway). The lab goes hand in hand with the lectures, and you work through it as though you are compromising a real multi-forest environment using native methods, rather than a command-and-control framework.
Overall, the coursework was a great refresher and helped solidify Red Team tactics that were previously covered in the CRTO, but without leveraging a C2. However, Sliver C2 is provided as an option, but not required.
The Exam:
As with all my exam reviews, out of respect for the Altered Security team, I will not reveal any specific details about the exam.
As the exam is self-service and can be started on demand, once begun, you are given 25 hours to gain Remote Code Execution on a specific number of fully patched servers, excluding the provided jump-box. The exam is designed to emulate an insider threat simulation/assumed compromise scenario.
I started my exam on the afternoon of December 26th, 2024, and completed my report by midnight, receiving confirmation that it was received the next day. For the most part, I understood the tasks of the exam and only got stumped on one task, which I eventually succeeded in completing. I’m keeping this very vague to preserve the integrity of the exam.

On December 30th, I received confirmation that I had passed the exam and was officially CRTP certified. I received my certificate on the 31st.
Closing Thoughts/Feedback:
- The lectures were truly great, and Nikhil did an excellent job.
- The labs are very practical and quite stable.
- The exam is both fair and reasonable, providing a balanced challenge.
Feedback:
- Provide greater detail on Defender bypassing via binary modification, or make it more concise, as we are not performing any modifications ourselves in the course, which is understandable at an entry level. While completing the course, I had hoped we would be conducting the alterations ourselves and even searched for Visual Studio.
- Dive deeper into the BloodHound GUI, as it is such a powerful tool. I believe it should be referenced more extensively, particularly on how to use it in a critical manner.
- Provide an official template for newcomers. While I personally had a few templates ready, individuals who may have never created a report would likely find it significantly more difficult.
